Remote work and cloud-based infrastructure reign supreme, secure access management has become a critical concern for organizations of all sizes. Enter HashiCorp Boundary Enterprise Crack – a game-changing solution that’s revolutionizing how businesses approach secure access control.
- What is HashiCorp Boundary Enterprise?
- The Evolution of Access Management
- Core Components of HashiCorp Boundary Enterprise
- Setting Up HashiCorp Boundary Enterprise
- Key Features of HashiCorp Boundary Enterprise
- Use Cases for HashiCorp Boundary Enterprise
- Best Practices for Implementing HashiCorp Boundary Enterprise
- Overcoming Common Challenges with Boundary Enterprise
- The Future of HashiCorp Boundary Enterprise
What is HashiCorp Boundary Enterprise?
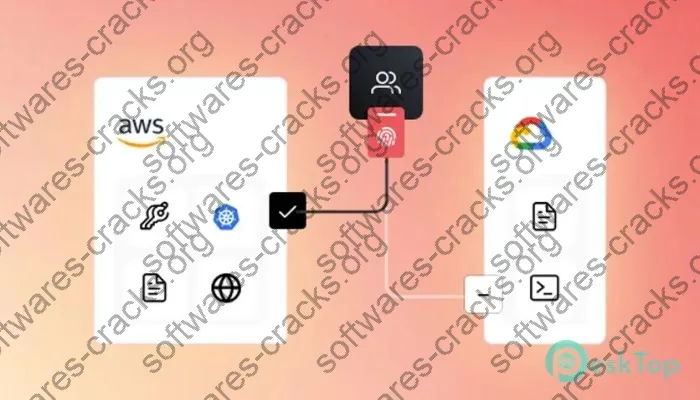
HashiCorp Boundary Enterprise is a cutting-edge access management platform designed to meet the complex security needs of today’s dynamic business environments. At its core, Boundary Enterprise provides identity-based access control for applications and systems, regardless of their location – be it on-premises, in the cloud, or spread across multiple environments.
Unlike its open-source counterpart, Boundary Enterprise offers enhanced features tailored for large-scale deployments:
- Advanced role-based access control (RBAC)
- Integrated multi-factor authentication (MFA)
- Comprehensive audit logging and reporting
- High availability and scalability options
- Enterprise-grade support and SLAs
These features make Boundary Enterprise a robust solution for organizations looking to implement a zero-trust security model while maintaining flexibility and ease of use.
The Evolution of Access Management
To truly appreciate the value of HashiCorp Boundary Enterprise, it’s essential to understand the evolution of access management:
- Traditional methods: Relied heavily on perimeter-based security, VPNs, and static credentials
- Modern approaches: Focus on identity-based access, just-in-time provisioning, and zero-trust principles
Boundary Enterprise represents the cutting edge of this evolution, offering:
- Dynamic access controls based on user identity and context
- Fine-grained permissions that can be adjusted in real-time
- Seamless integration with existing identity providers and infrastructure
This shift allows organizations to move beyond the limitations of traditional VPNs and firewall rules, embracing a more flexible and secure approach to access management.
Core Components of HashiCorp Boundary Enterprise
See also:
Identity-based Access Control
At the heart of HashiCorp Boundary Enterprise Activation Key lies its identity-based access control system. This component:
- Authenticates users based on their identity, not just credentials
- Integrates with popular identity providers like Okta, Azure AD, and Google Workspace
- Supports just-in-time access provisioning to reduce standing permissions
Dynamic Host Catalogs
Boundary Enterprise’s dynamic host catalogs allow for:
- Automatic discovery and categorization of resources across multiple environments
- Real-time updates as infrastructure changes
- Efficient management of large-scale, dynamic environments
Session Management and Monitoring
With Boundary Enterprise, you get:
- Real-time visibility into active sessions
- Ability to terminate sessions instantly if suspicious activity is detected
- Detailed logs for auditing and compliance purposes
Credential Brokering
This feature:
- Eliminates the need for users to manage or even see credentials
- Provides temporary, just-in-time credentials for authorized access
- Enhances security by reducing the risk of credential theft or misuse
Setting Up HashiCorp Boundary Enterprise
Getting started with HashiCorp Boundary Enterprise Serial Key involves a few key steps:
- System Requirements:
- Supported operating systems: Linux, macOS, Windows
- Minimum 4 CPU cores and 8GB RAM for production deployments
-
Storage requirements vary based on logging and auditing needs
-
Installation Process:
- Download the enterprise version from our site
-
Choose between binary installation or container-based deployment
-
Initial Configuration:
- Set up your initial admin account
- Configure your identity provider integration
- Define your first set of scopes and targets
Key Features of HashiCorp Boundary Enterprise
Multi-factor Authentication (MFA) Integration
Boundary Enterprise takes security a step further by offering:
- Seamless integration with popular MFA providers
- Support for various authentication methods (SMS, app-based tokens, hardware keys)
- Customizable MFA policies based on user roles or resource sensitivity
Role-based Access Control (RBAC)
The RBAC system in Boundary Enterprise allows for:
- Granular control over user permissions
- Easy management of access rights at scale
- Dynamic role assignments based on user attributes or group memberships
Audit Logging and Reporting
For compliance and security analysis, HashiCorp Boundary Enterprise Crack provides:
- Detailed logs of all access attempts and sessions
- Customizable reports for various stakeholders
- Integration with popular SIEM tools for advanced analytics
High Availability and Scalability
Enterprise-grade features include:
- Multi-cluster deployments for improved resilience
- Automatic load balancing and failover
- Horizontal scaling to support growing organizations
Integration with Existing Infrastructure
Boundary Enterprise plays well with others, offering:
- APIs for seamless integration with CI/CD pipelines
- Support for popular infrastructure-as-code tools like Terraform
- Compatibility with a wide range of cloud providers and on-premises systems
Use Cases for HashiCorp Boundary Enterprise
Securing Remote Access for Distributed Teams
In today’s remote-first world, Boundary Enterprise shines by:
- Providing secure access to internal resources without VPNs
- Enabling fine-grained control over who can access what, when, and from where
- Simplifying the onboarding and offboarding process for remote workers
Managing Access to Cloud Resources
For organizations leveraging multi-cloud or hybrid cloud environments, Boundary Enterprise offers:
- Unified access control across different cloud providers
- Dynamic discovery and cataloging of cloud resources
- Consistent security policies regardless of resource location
Streamlining DevOps Workflows
DevOps teams benefit from:
- Just-in-time access to development and production environments
- Automated access provisioning through CI/CD pipelines
- Reduced friction between security requirements and development speed
Compliance and Regulatory Requirements
HashiCorp Boundary Enterprise Activation Code helps organizations meet various compliance standards by providing:
- Detailed audit trails for all access events
- Enforced separation of duties through granular RBAC
- Controlled access to sensitive data and systems
Best Practices for Implementing HashiCorp Boundary Enterprise
- Plan Your Deployment:
- Map out your existing infrastructure and access needs
- Define clear goals for your access management strategy
-
Start with a pilot project before full-scale deployment
-
User Onboarding and Training:
- Provide comprehensive training for both administrators and end-users
- Create clear documentation and user guides
-
Offer ongoing support and feedback channels
-
Ongoing Maintenance and Updates:
- Regularly review and update access policies
- Keep the Boundary Enterprise software up to date
- Conduct periodic security audits and penetration testing
Overcoming Common Challenges with Boundary Enterprise
Integration with Legacy Systems
While Boundary Enterprise is designed for modern environments, many organizations still rely on legacy systems. To bridge this gap:
- Use Boundary’s extensible plugin system to create custom connectors
- Implement a phased approach, gradually moving systems under Boundary’s control
- Leverage HashiCorp’s professional services for complex integration scenarios
See also:
User Adoption and Change Management
Introducing a new access management system can be met with resistance. To smooth the transition:
- Communicate the benefits clearly to all stakeholders
- Provide ample training and support during the rollout
- Gather and act on user feedback to continuously improve the experience
Performance Optimization
As your deployment grows, you may need to optimize for performance:
- Monitor system metrics closely and scale resources as needed
- Use caching and load balancing to improve response times
- Consider geographical distribution for global organizations
The Future of HashiCorp Boundary Enterprise
HashiCorp continues to innovate, with upcoming features rumored to include:
- Enhanced machine learning capabilities for anomaly detection
- Expanded integration options with popular SaaS platforms
- Improved self-service capabilities for end-users
As the landscape of secure access management evolves, HashiCorp Boundary Enterprise Crack is poised to remain at the forefront, adapting to new challenges and technologies.
I appreciate the upgraded layout.
The tool is definitely awesome.
I would definitely recommend this software to professionals needing a top-tier solution.
I would definitely recommend this software to professionals looking for a top-tier product.
The responsiveness is so much enhanced compared to older versions.
I would strongly endorse this tool to professionals needing a robust platform.
The application is really fantastic.
The new functionalities in update the newest are so great.
I really like the upgraded workflow.
The software is definitely great.
The recent updates in update the newest are incredibly awesome.
It’s now a lot more user-friendly to get done tasks and track content.
It’s now far simpler to get done projects and track data.
The software is absolutely impressive.
The program is definitely great.
I would strongly recommend this tool to professionals needing a high-quality solution.
I love the enhanced workflow.
The new updates in version the newest are extremely great.
This platform is definitely awesome.
The new enhancements in version the latest are incredibly great.
The application is definitely great.
It’s now much easier to get done work and track information.
I absolutely enjoy the improved UI design.
The new enhancements in release the newest are extremely awesome.
I absolutely enjoy the improved layout.
I would definitely suggest this program to professionals needing a powerful product.
The performance is a lot faster compared to the original.
I really like the improved dashboard.